What is cryptography?
Table of content
⚡️ What is cryptography, and how does it work?
In the presence of malevolent third parties known as adversaries, crypto enables secure communication. The encryption process transforms plaintext into an unreadable code, using a specific algorithm and unique key.
⚡️ Is blockchain cryptography?
Blockchain technology is made up of two distinct cryptographic formulas: asymmetric key algorithms and hash functions. Utilizing the SHA-256 hashing algorithm, each participant can create one unique version of the blockchain based on their own view. This enables any individual to understand and access a single representation of the entire chain, while simultaneously preserving its accuracy across all other participants connected to it.
⚡️ Who created Bitcoin?
Satoshi Nakamoto.
Who is Satoshi Nakamoto? Shrouded in secrecy, the true identity of Satoshi Nakamoto – the revolutionary pioneer behind Bitcoin, the world's leading cryptocurrency – continues to elude us. Nakamoto was the first miner of the bitcoin chain and released a technical paper for the digital currency.
⚡️ Is Elon Musk investing in bitcoin?
Elon Musk recently made a game-changing declaration with his large investments in Bitcoin, Etherium and Dogecoin. This news is sure to be felt throughout the cryptocurrency world, entirely transforming perspectives on digital finance from those invested within this realm.
Cryptography is the study and application of secure messaging. By using cryptography, digital currency transactions can be pseudonymous, safe, and “untrusted” without the need for a bank or other middleman.
The name “coin” comes from the Greek root word for “secret.” This is a very broad term that encompasses many forms of digital money. Cryptography, as the study and practice of sending secure, encrypted messages or data between two or more parties, is what cryptocurrency is all about. Cryptography is the process of writing or reading secret messages.
Cryptography is an essential technique for protecting information, allowing it to be securely sent and received by the intended recipient alone. Encrypting messages, we help ensure that only those who are meant to read them can access and decipher their content. The receiver then decrypts the message, allowing them to view its contents.

Cryptography is an essential part of our digital lives, from the emails we write to sending data on Google. With cryptocurrency transactions enabled by cryptographic processes, there's no need for third-party organizations or government involvement – plus all of your financial information stays secure and private! Every transmission that you make is automatically encrypted and decrypted without any extra effort needed; giving you peace of mind each time you use a form of payment online.
Why is cryptography so vital?
The complex math behind Cryptocurrencies ushered in the 2009 creation of Bitcoin by enigmatic figure(s) known as Satoshi Nakamoto. Through a cryptography-based paper published online, this revolutionary currency was officially declared to the world.

The double-spending problem posed the most arduous challenge to Satoshi Nakamoto, as Bitcoin is nothing more than a conglomeration of code. How can we ensure that someone isn't spending multiple versions of their money? To solve this issue, Nakamoto employed public and private key encryption; an esteemed encrypting process commonplace today.
The use of public and private key encryption, as seen in Bitcoin (as well as Ethereum and other cryptocurrencies), allows strangers to conduct secure transactions without the need for a “trusted intermediary” such as a bank or PayPal in the middle.
Are you aware of the difference between public and private key encryption?
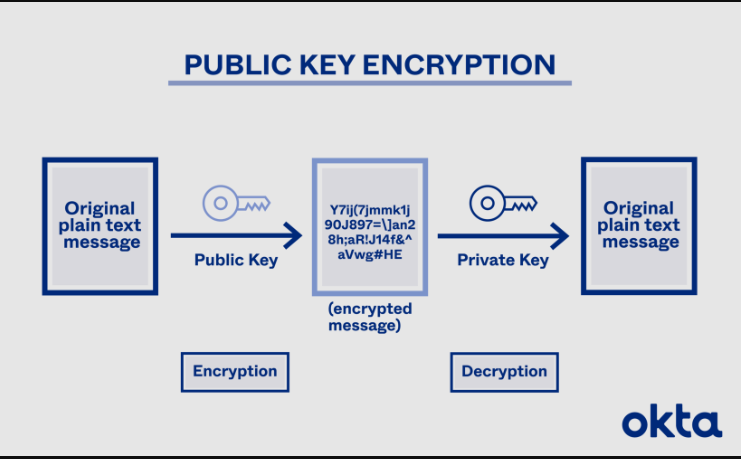
All users have a private key (essentially a very strong password) from which a linked public key is generated by the Bitcoin network. You are free to share your public key with anybody; in fact, it's all anybody needs to send you bitcoins. To unlock those hidden funds, you must have a private key.
Bitcoin's popularity is fueled by its peer-to-peer network and sophisticated cryptographic techniques, which authenticate transactions.
By using a data-string operation called “hashing,” your public key is generated from your private key. Hashing is very difficult to reverse, so no one can access your private key by only knowing your public key.
Your Bitcoin is yours to keep as long as you have your private key since your public and private keys are linked.
Not having an intermediary has several effects. One is that Bitcoin transactions are irreversible (because there is no credit card company to contact if you make a blunder). But that's not a deficiency; rather, it's an asset: permanent transactions are essential to addressing the double-spending problem.
The rest of the solution is bitcoin-blockchain, which is a massive decentralized ledger (think bank balance sheets) that documents every transaction and is constantly verified and updated by all of the network's machines.

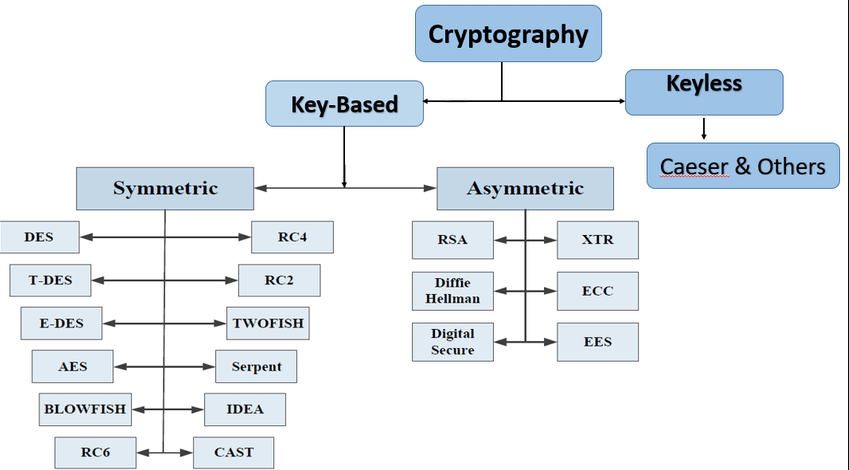
Cryptography Techniques
In cryptography, data is made safe and sound using mathematically sophisticated encoding and decoding techniques.
It conceals information by making use of techniques such as microdots, word merging, or picture coverups to make it appear invisible to those not trained in this art. With cryptography, hidden messages can be securely communicated without fear of interception!
In the present world, where computers run the show, cryptography is commonly related to encoding plain text into encrypted text (which is called encryption) and then reversing this process (known as decryption). Those who practice this technique are known as cryptographers.
The following represent the four main functions of modern cryptography:
- Privacy. Knowledge cannot be understood by those who were not intended to receive it.
- Integrity. Information cannot be changed in transit or stored without being detected.
- Irrevocability. The originator/sender of the information cannot later deny his or her intentions to create or transmit it.
- Authentication. The sender and receiver can verify each other's identity and the information's origin/receiver.

Cryptosystems deliver a secure system experience by fulfilling the essential security prerequisites. Cryptosystems are frequently regarded as exclusively mathematical procedures and computer programs; however, they also include human behavioral regulation, such as establishing difficult passwords, shutting down useless systems, and refusing to reveal secret methods to strangers.
Proprietary or patented algorithms
Cryptosystems provide a crucial layer of protection for data sent over networks, ensuring that communication between devices remains secure. By deploying advanced cryptographic tactics such as encryption and authentication, they effectively secure confidential information from malevolent entities that seek to gain access or cause harm. Furthermore, cryptosystems serve as an essential tool to guarantee the validity of messages in transit—verifying only legitimate users are able to view them!
A suite of intricate ciphers, protocols and software penned for operating systems (OS) and networked computer systems carries out a series of processes to guarantee information security. At the foundation are algorithms that encrypt messages, authenticate them, then transmit keys in sets.
- Generating public and private key pairs is critical for the secure encryption and decryption of data.
- Digital signing and authentication of messages
- key exchange.
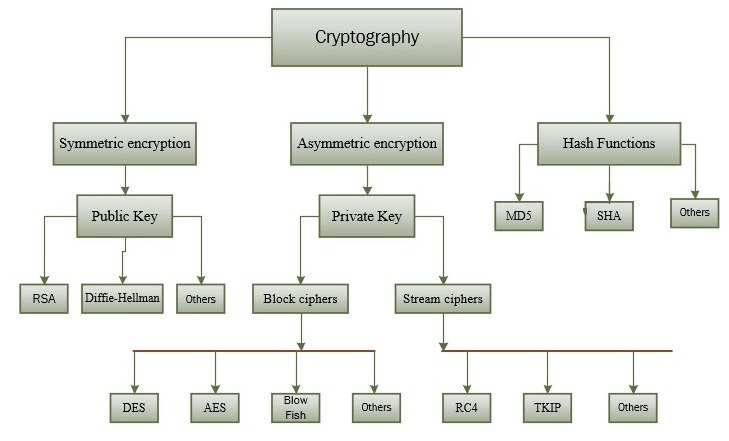
Three basic types of encryption and data protection methods.

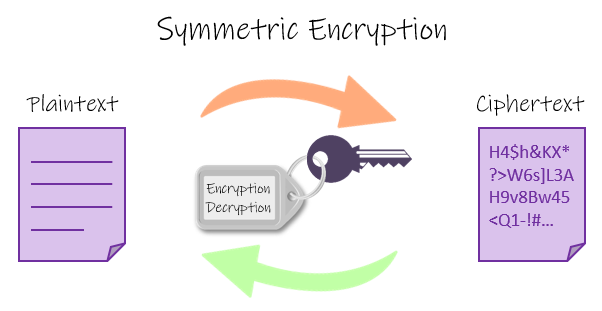
A block cipher, otherwise known as a fixed-length encryption algorithm, can be utilized to safeguard data by the creator/sender through encryption and decrypted by the recipient using an exclusively-established secret key. The Advanced Encryption Standard ( AES encryption ) is one example of symmetric key cryptography.
The Advanced Encryption Standard (AES encryption) is a NIST-approved Federal Information Processing Standard (FIPS 197) for safeguarding sensitive data. The standard is authorized by the United States government and widely used in the commercial sector.

The U.S. government gave its blessing to the use of AES for sensitive data in June 2003. This globally recognized, freely available protocol is implemented in hardware and software designs. AES encryption is the new standard for data encryption, replacing DES and DES3. To prevent brute force attacks and other security problems, it uses longer keys—128, 192, or 256 bits.
This figure compares symmetric and asymmetric encryption.
In contrast to symmetric cryptography which requires just one key, asymmetric crypto uses two distinct keys in order to encrypt and decrypt data.
From the perspective of public-key encryption, a sender needs to generate two keys: a private key which should remain undisclosed and is only known to the proprietor unless they choose otherwise; and a public key, used for encrypting messages. This pair must always be maintained as one cannot function without the other.
Here are a few ways public-key cryptography can be used:
- RSA is widely used on the Internet.
- Elliptic Curve Digital Signature Algorithm (ECDSA), used by Bitcoins
- By the security standards of NIST and FIPS 186-4, Digital Signature Algorithm (DSA) is an essential federal information processing standard for digital signature authentication. Bitcoin supports DSA along with two other algorithms.
Diffie-Hellman key exchange

Hash functions are powerful mathematical algorithms that transform a given input into an output of fixed size. Through this process, data integrity is secured in cryptography. SHA-1 (Secure Hash Algorithm 1) is one of the most widely used hash functions currently in circulation.
Cryptography issues
Even though cryptography can secure communications, attackers still have ways to bypass it and break into computers that manage encryption. Poor implementations like using default keys make this even easier for them. On the other hand, cryptographic security enhances protection against malicious actors trying to access encrypted messages or data.

In anticipation of the quantum computing era, NIST initiated a call for papers from mathematicians and scientists to develop new public-key cryptography standards. This was due to increasing anxiety over quantum computers' impressive computational abilities that could potentially compromise existing encryption techniques. Since 2016, NIST has been devotedly working on these fresh cryptographic models in order to prepare for this future breakthrough.
In comparison to traditional computers, quantum computing relies on qubits-which can depict both 0 and 1 simultaneously. Thus, enabling it to perform two operations at once. Although NIST anticipates that a large scale quantum computer won't be built in the upcoming decade, the present technology requires standardization of commonly accepted algorithms for public-key cryptography which are immune from any possible attack by a quantum computer.
Why is cryptography so important?
As the Internet is used increasingly for business and personal purposes, cryptography has become an invaluable asset in protecting security-sensitive data from being accessed by unauthorized users.
With its combination of code, key, and calculations to lock away information safely within encrypted files, this method proves far better than any other when it comes to keeping your confidential records secure. In today's digital world, encryption plays a critical role in safeguarding your sensitive data from preying eyes!
Telephones used to be tapped all the time- Authorities didn't need a warrant, they could just listen in on whoever they wanted. However, with cryptography, this worry is now gone as any message you send can only be decoded by the intended recipient. This goes for everything from personal messages to confidential bank information.



